I started using Salesforce in 2004. The company I was with was piloting it, and they eventually became a Salesforce customer. During that decade, there were companies popping up everywhere offering SaaS, which was the fad of its time. As the B2B cloud apps space has matured, a lot more structure has entered into the fray. But over the last 6 years, we've been careening into a world where those startup ventures, out of somebody’s garage, or one-bedroom apartment, will be impossible to get off the ground. And we’re doing it to ourselves.
Your first customer
The lifeblood of an idea is customer validation. As Scott Adams put it, “If you can get somebody to physically move their body to use what you’re selling, that’s a good sign you’ll succeed.” At the earliest stages of a successful startup, the venture is both at its highest level of flexibility and its lowest level of capital resources. So your first customers act as the gateway to show that people will “move their body.” They spark the proofs needed to go get VC money, or go “all in.”
In The Innovator's Dilemma, we learn that the way disruptors move into the market is that they start with a small and very low-cost use case, and they expand upon it to disrupt the incumbents. Incumbents don’t have the flexibility of a startup by the very fact that they must establish fixed processes to stabilize cash flow.
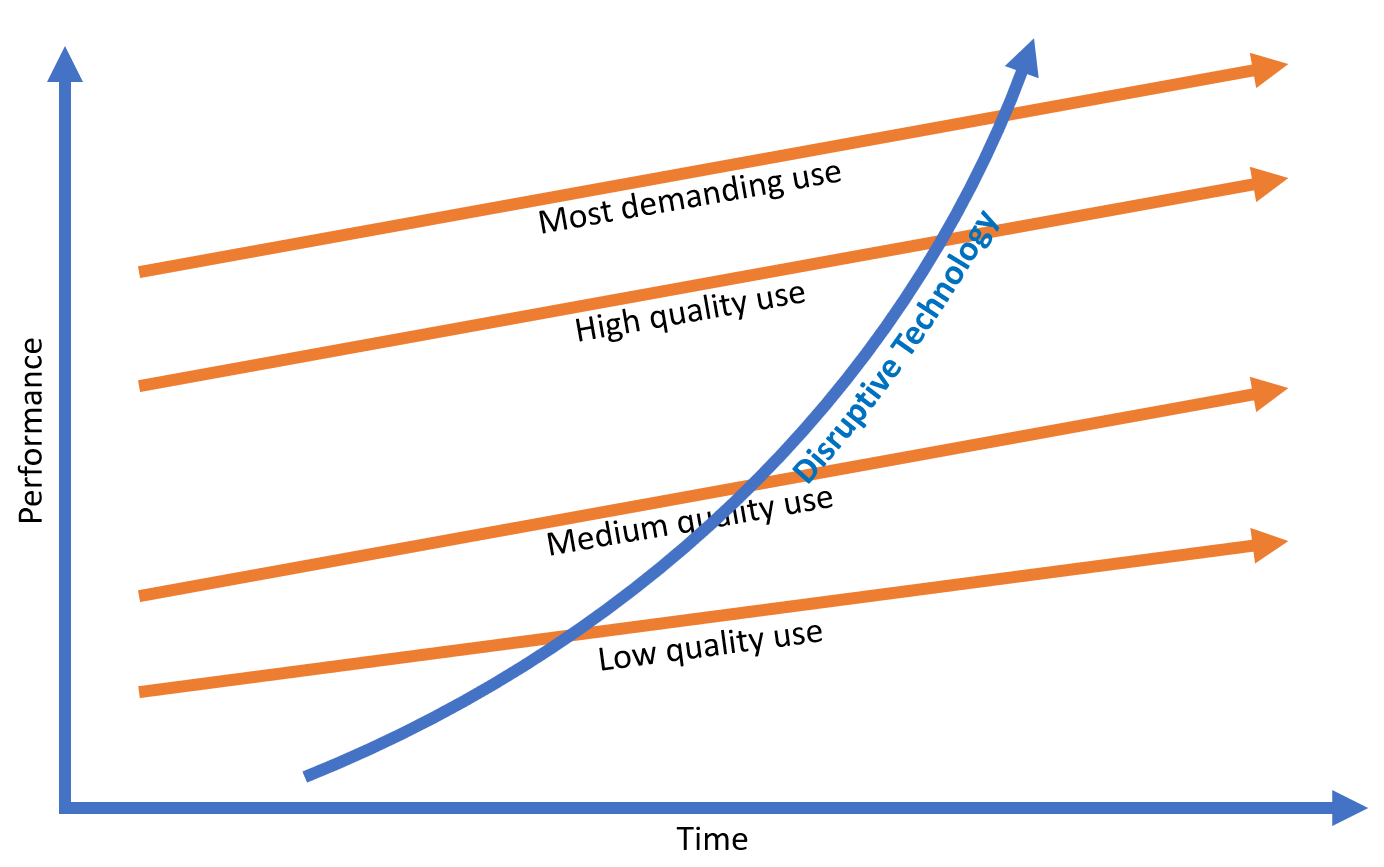
Innovator's Dilemma
That stability is what keeps them from being flexible. So what must the incumbents do to safeguard their lead? They have to put up barriers to entry. They have to create hurdles that are so high as to make the first customer impossible to acquire, and that’s the ecosystem we are experiencing in the cloud software space.
Bill Gurley spoke about exactly this in relation to regulations coming out of Washington DC during the ALL IN SUMMIT.
But I want to point to another set of barriers that are putting a knife in the Enterprise Software space and pushing Venture Capitalists into less and less evidentiary investments… security compliance. Nobody would argue that we shouldn’t secure data, or that we should be irresponsible with data. But the modern compliance requirements would have easily put Salesforce on a path to never getting off the ground. Just for kicks, put yourself in the shoes of a developer in a garage trying to get something off the ground, and show compliance to the following questions:
Is the assessment for the entire company, or a particular functional area or risk control topic?
What is the name of the product, service, or system being provided by the vendor, processor, or third party?
Provide a brief description of the types of services being performed by the third party?
Enter the URL of any web site (s) applications that are in scope for the assessment?
What is the URL of the company relevant to the services being scoped for the assessment?
Comments:
Does the company provide personnel or staff augmentation?
Does the company or services require direct end-user interaction?
Does the company utilize the services of Fourth-Nth parties for the delivery of the product, service or system?
Do the products, services, or system require network connectivity between parties?
Do the products, services, or systems require remote access between parties?
Do the products, services, or systems require system to system integration?
Do the products, services, or systems include any classification of personally identifiable information?
Are technology or software applications provided?
List the applications provided that are in scope.
What type of technology or software is being provided? Select all that apply from the list below. (Allows other)
Does this assessment include Cloud Hosting Services?
What service hosting models are provided as part of this service? Select all that apply from the list below.
What type of Cloud Computing Services are being provided? Select all that apply from the list below.
What type of Cloud Deployment Models are provided? Select all that apply from the list below.
Comments:
Lead Assessee contact name:
Assessee contact job title:
Assessee business contact information:
Type of Assessment (Onsite or Virtual)
Date of Assessment: (Import expects YYYY-MM-DD format)
Location(s) where the assessment was performed:
Document Request
Documentation that defines the Enterprise Risk Management program requirements (e.g., Enterprise risk governance plan, policies and procedures)
Documentation that describes the organization's process for addressing contract clauses within fourth party (vendor or service provider) agreements and including evidence that the organization's required data protection requirements (e.g., standard provisions, addendums, appendices) have been included in the contracting process
Documentation that defines the organization's guidelines and process for management and approval of exception handling for required contract terms
Documentation that defines the requirements for selection, due diligence and management of any Fourth-Nth parties.
A copy of the formal criteria and methodology used to identify the inherent and residual risk associated to any third party entity involved in the delivery of the services.
Documentation of the organization's information security policies
Documentation of the organization's information security standards
A copy of its current, approved Information Security (IS) organizational document, including IS roles and responsibilities
Documentation that defines Information Asset Management Program e.g., policies, procedures or standards
Documentation regarding the policies, procedures, and logs used for tracking inbound and outbound media shipments
Organization documentation of its process for restricting the use of removable devices
Documentation regarding the organizations encryption key management policy, procedures or standards
Documentation reflecting the current human resource security and background investigation policy and procedures, including but not limited to evidence of completion of background checks prior to employment
Documentation of its process for handling involuntary/voluntary separations
Documentation regarding the organization's policies, standards or guidelines for environmental controls
Documentation regarding its visitor management program and a copy of the organization's visitor logs from the past 90 days
Obtain the policies/procedures related to operational procedures. Include a recent copy of the master change log for all target systems for the past six months
Security patch process, including the name of the tool used for patch management
A list of application security risks that are documented as part of the application security program, and review the most recent application security report
Documentation of the policies, procedures, and standards that are in place for website setup and security, including architecture diagrams for any in scope web applications
Access control policy and procedure documentation
Corporate password policy and procedures documentation
Documentation regarding the process for reviewing, revoking or disabling access to inactive accounts, including a sample user access report
Documentation regarding the policies and procedures to prevent unauthorized access to unattended systems
Policy and procedures for remote access
Documentation related to the use of a remote desktop support function
All policies, standards and procedures related to SDLC controls
Documents that define the organization's SDLC requirements, criteria, and the process to conduct security reviews
Documentation regarding the standard policies and procedures to address security in the development process, including code reviews for target systems or applications
Documentation regarding the policies and procedures for performing a privacy impact assessment, including the lists of projects in development or completed in the last 12 months
A copy of its procedures related to the use and protection of production data being utilized in the test environment(s)
A copy of the incident management policy(ies), plans and procedures
Documentation detailing resources and tools available for information security/information technology incident handling including recommended practices for securing networks, systems and applications
A copy of its business resilience policy, as well as the documentation detailing business resilience roles and responsibilities, processes and management reporting
The results of the latest enterprise and location level risk assessment(s) performed
Documentation regarding its backup and replication processes and capabilities, including an executive summary of the last test of the backup process and the replication process (as appropriate)
Business resilience exercise procedures and related reference information for critical systems, applications or business processes
A copy of its most recent infectious disease plan
Documentation that defines organizational structures and oversight functions including any policies, standards, and procedures for compliance with legal, regulatory, and standards obligations
Documentation of its Environmental, Social, and Corporate Governance (ESG) risk management program, including processes for reporting, documenting and monitoring its commitments
A copy of its professional ethics and business practices program and related operational procedures and/or guidelines
Documentation on policy and procedures for end user or endpoint security configuration standards
Documentation regarding the process to maintain up-to-date IDS/IPS signatures, including the most report or screen shot of the IDS/IPS signatures
Documentation regarding the deployment of firewalls or devices to protect the organization from outside entities, including a network diagram of the target systems or applications
Documentation regarding the policies and procedures for deployment of IDS/IPS systems
Compliance documentation regarding its client-scoped data inventory, the data flow, in scope privacy regulatory jurisdictions, privacy policy and procedures, including any data classification policy or procedures
Documentation regarding organizational structure and scope of the data privacy or data protection program, including policies, standards and procedures related to privacy program management functions.
Documentation regarding the delivery and schedule of privacy awareness training to the organization and its constituents
Documentation including any data confidentiality agreements, operating procedures or any related instructions, statements of work, compliance requirements, applicable terms and conditions, regarding scoped data
Privacy Notice documentation that includes a sample of the current web privacy notice(s) applicable to the services provided; description of the mechanism to provide access to the Notice and documentation regarding the policies, procedures or guidelines for maintenance of the notice
Documentation of policies, procedures or guidelines that describe the privacy incident reporting, notification, communications and post-incident handling regarding unauthorized disclosure or breach of personal information
Documentation regarding the organization's legal or regulatory authorizations, process for handling privacy inquiries, complaints or disputes from individuals; and any publicly available privacy regulator complaints, findings or court ruling(s) concerning privacy
A copy of the current, approved system configuration and hardening standards for each type of operating system in use for workstations, servers and network devices
Documentation regarding the usage of Cloud Service Provider (CSP) services related to security policies, controls and delineation of security responsibilities, including component and system configuration standards
Documentation on the company's governance process for cloud hosting, include the internal and external audit assurance responsibilities; the Cloud Hosting Provider's independent audit reports (e.g., Service Operational Control-SOC, ISO Certification) for their cloud hosting services and any CSP audit program documentation
Is there a formalized risk governance plan approved by management that defines the Enterprise Risk Management program requirements?
Does the risk governance plan include risk management policies, procedures, and internal controls?
Do fourth parties (e.g., backup vendors, service providers, subcontractors, equipment support maintenance, software maintenance vendors, data recovery vendors, hosting providers, etc.) have access to scoped systems and data or processing facilities?
Is there a documented third party risk management program in place for the selection, oversight and risk assessment of fourth Parties (e.g., subcontractors, suppliers, service providers, dependent service providers, sub-processors) in scope for the services?
For all organizational entities (e.g., vendor's vendors, subcontractors, fourth parties, Nth parties) is there a contractual relationship that extends obligations to each entity?
Does the third party risk management program include an assigned individual or group responsible for capturing, maintaining, and tracking Information Security, Privacy, or other issues?
Is there a set of information security policies that have been approved by management, published and communicated to constituents?
Do the information security policies and procedures establish requirements for the protection of information that is processed, stored or transmitted on external systems?
Have all information security policies and standards been reviewed in the last 12 months?
Are responsibilities for asset protection and for carrying out specific information security processes clearly identified and communicated to the relevant parties?
Are information security personnel (internal or outsourced) responsible for information security processes?
Do all projects involving Scoped Systems and Data go through some form of information security assessment?
Is there an asset management program approved by management, communicated to constituents and an owner to maintain and review?
Is there an asset Inventory list or configuration management Database (CMDB)?
Is there an acceptable use policy for information and associated assets that has been approved by management, communicated to appropriate constituents, and assigned an owner to maintain and periodically review the policy?
Is there a process to verify return of constituent assets (computers, cell phones, access cards, tokens, smart cards, keys, etc.) upon termination?
Is Information classified according to legal or regulatory requirements, business value, and sensitivity to unauthorized disclosure or modification?
Is there a policy or procedure for information handling consistent with its classification that has been approved by management, communicated to appropriate constituents and assigned an owner to maintain and periodically review e.g., authorized parties, encryption, public cloud storage, removable media, classification labeling, etc.?
Is there a data retention/destruction requirement that includes information on live media, backup/archived media, and information managed by fourth parties?
Is Scoped Data sent or received via physical media?
Is Scoped Data sent or received electronically?
Is regulated or confidential scoped data stored electronically with data protection safeguards e.g., full-disk encryption, databases, files, encryption keys, etc.?
Are Human Resource policies and/or procedures approved by management, communicated to constituents and an owner to maintain and review?
Is there a process to remove access to systems containing scoped data within 24 hours for terminated constituents?
Is there a physical security program approved by management, communicated to constituents, and has an owner been assigned to maintain and review?
Are assessment of the physical and environmental hazards conducted prior to establishing the location or site of a facility where systems reside?
Are visitors permitted in the facility?
Is there an operational change management/Change Control policy or program that has been documented, approved by management, communicated to appropriate Constituents and assigned an owner to maintain and review the policy?
Are Information security requirements specified and implemented when new systems are introduced, upgraded, or enhanced?
Is there an access control program that has been approved by management, communicated to constituents and an owner to maintain and review the program?
Are constituents able to access Scoped data?
Are unique IDs required for authentication to applications, operating systems, databases and network devices?
Is there a password policy for systems that transmit, process or store Scoped systems and data that has been approved by management, communicated to constituents, and enforced on all platforms and network devices? If no, please explain in the Additional Information field.
Is password reset authority restricted to authorized persons and/or an automated password reset tool?
Does the password policy require changing passwords at regular intervals?
Does the password policy require keeping passwords confidential?
Are user IDs and passwords communicated/distributed via separate media e.g., e-mail and phone?
Does the password policy require changing passwords when there is an indication of possible system or password compromise?
Is Multi-factor Authentication deployed?
Does system policy require terminating or securing active sessions when finished e.g., end user devices or systems?
Is there a process for reviewing access e.g., periodical review, role changes etc.?
Are inactive Constituent user IDs disabled and deleted after defined periods of inactivity?
Are applications used to transmit, process or store scoped data?
Are development, test, and staging environment separate from the production environment?
Are Scoped Systems and Data used in the test, development, or QA environments?
Is application development performed?
Is there a secure software development lifecycle policy that has been approved by management, communicated to appropriate constituents and an owner to maintain and review the policy?
Are applications evaluated from a security perspective prior to promotion to production?
Are identified security vulnerabilities remediated prior to promotion to production?
Is a web site or web application supported, hosted or maintained that processes scoped systems and data?
Are security configuration standards documented for web server software?
Is an Application Programming Interface (API) available to clients?
Is there a formal security program established to include API security reviews?
Is Scoped Data encrypted in transit within the API for both request and response?
Is there an established Cybersecurity Incident Management Program that has been approved by management, communicated to appropriate constituents and an owner to maintain and review the program?
Is there a formal Incident Response Plan that includes an escalation procedure?
Are events on Scoped Systems or systems containing Scoped Data relevant to supporting incident investigation regularly reviewed using a specific methodology to uncover potential incidents?
Does regular security monitoring include malware activity alerts such as uncleaned infections and suspicious activity?
Is there a staffed form of communications (e.g., e-mail, web form, phone, etc.) available to customers/clients 24/7/365 to report security incidents?
Is there an established Business Resilience Program that has been approved by management, communicated to appropriate constituents, and an owner to maintain and review the program?
Do the products and/or services specified in the scope of this assessment fall within the scope of the Business Resiliency program?
Is there a formal, documented Information Technology Disaster Recovery exercise and testing program in place?
Are there any dependencies on critical third party service providers?
Has the organization established processes and formal agreements for third party service providers to provide immediate notification in the event of a disruption that impacts delivery of the products and/or services they provide?
Is there a pandemic/infectious disease outbreak plan?
Does the pandemic plan include a preventive program to reduce the likelihood that an organization's operations will be significantly affected by a pandemic event?
Is there a policy or process for the backup of production data?
Is there a formal process focused on identifying and addressing risks of disruptive events to business operations?
Are formal business continuity procedures developed and documented?
Has senior management assigned the responsibility for overall management of business disruption events, critical response and recovery efforts?
Is scoped data backed up and stored offsite?
Is there a data retention policy or process with a retention schedule for scoped data?
Is there a plan for managing a data recovery effort in the aftermath of a successful data compromising cyberattack e.g., ransomware, data-wipe malware?
Are there policies and procedures to ensure compliance with applicable legislative, regulatory and contractual requirements?
Is there an internal audit, risk management, or compliance department, or similar management oversight function with responsibility for tracking resolution of outstanding regulatory or compliance issues?
Does the organization have a formalized Environmental, Social, and Corporate Governance (ESG) program or set of policies and procedures approved by management?
Is a web site(s) maintained or hosted for the purpose of advertising, offering, managing, or servicing accounts, products or services to clients' customers?
Is there a compliance program or set of policies and procedures in place to restrict activities or transactions for sanctioned countries (e.g., country blocking)?
Is there a compliance program or set of policies and procedures to address bribery, corruption, prohibition of providing monetary offers, incentives, or improper actions that create unfair advantage in business practices?
Is there a compliance program or set of policies and procedures that address Anti-Trust and Anti-Competitive Business Practices?
Is there a documented internal compliance and ethics program?
Is there a documented policy or set of procedures for Ethical Sourcing?
Are documented policies and procedures maintained to enforce applicable legal, regulatory or contractual cybersecurity compliance obligations?
Is there a compliance program or set of policies and procedures that address internal and external Fraud Detection and Fraud Prevention?
Is there a records retention policy and retention schedule covering paper and electronic records, including email in support of applicable regulations, standards and contractual requirements?
Are there documented policies and procedures that address prevention of modern slavery and human trafficking?
Is there a compliance program and procedures that address health and safety risks?
Are End User Devices (Desktops, Laptops, Tablets, Smartphones) used for transmitting, processing or storing Scoped Data?
Are there end user device security configuration standards?
Are defined procedures in place to identify and correct systems without anti-virus at least weekly for all end user devices?
Are Constituents allowed to utilize mobile devices within your environment?
Is there a mobile device management program in place that has been approved by management and communicated to appropriate Constituents?
Can Constituents access corporate e-mail using mobile devices?
Are non-company managed computing devices used to connect to the company network?
Are any mobile devices with access to Scoped Data Constituent owned (BYOD)?
Are collaborative computing devices and applications (e.g., networked white boards, cameras, and microphones) used for accessing, transmitting, processing, or storing Scoped data?
Is there a policy that defines network security requirements that is approved by management, communicated to Constituents and has an owner to maintain and review?
Are there security and hardening standards for network devices, including Firewalls, Switches, Routers and Wireless Access Points (baseline configuration, patching, passwords, Access control)?
Are default passwords changed or disabled prior to placing network devices into production?
Does network device patch management include testing of patches, service packs, and hot fixes prior to installation?
Is every connection to an external network terminated at a firewall (e.g., the Internet, partner networks)?
Are network or security technologies used to establish and enforce security requirements and block unauthorized traffic between segregated systems and other networks and systems?
Are all firewall and other network Access Control List (ACL) rules reviewed and updated at least quarterly and include identification and removal of networks, sub networks, hosts, protocols or ports no longer in use?
Is there a policy that defines the requirements for remote access from external networks to networks containing Scoped Systems and Data that has been approved by management and communicated to constituents?
Are encrypted communications required for all remote network connections from external networks to networks containing Scoped Systems and Data?
Does the organization maintain policies and procedures for the access to and the usage of collaborative computing devices or applications e.g., networked white boards, cameras, and microphones?
Are Network Intrusion Detection capabilities employed e.g., appliance, software, etc.?
Is there a DMZ environment within the network that transmits, processes or stores Scoped systems and data e.g., web servers, DNS, directory services, remote access, etc.?
Is there a wireless policy or program that has been approved by management, communicated to appropriate constituents and an owner to maintain and review the policy?
Is there collection, access , processing, disclosure, or retention of any classification of personal information or personal data of individuals on behalf of the client?
Has the organization developed and maintained a formal privacy program for the protection of personal information collected, accessed, transmitted, processed, disclosed, or retained on behalf of the client?
Is client scoped data collected, accessed, transmitted, processed, disclosed, or retained that can be classified as personally identifiable financial information under the Gramm-Leach-Bliley Act (GLBA)?
Is client scoped data collected, accessed, processed, disclosed, or retained that can be classified as consumer report information or derived from a consumer report under the Fair and Accurate Credit Reporting Act (FACTA)?
Is client scoped data collected, accessed, transmitted, processed, disclosed, or retained that can be classified as Protected Health Information (PHI) or other higher healthcare classifications of privacy data under the U.S. Health Insurance Portability and Accountability Act (HIPAA)?
Are there documented policies and procedures to detect and report unauthorized acquisition, use, or disclosure of PHI client scoped data?
Is client scoped data collected, accessed, transmitted, processed, or retained that can be classified under U.S. State Privacy Regulations (e.g., CA, MA, NY, NV, VA, WA, CO etc.)?
Is client scoped data collected, accessed, transmitted, processed, disclosed, or retained that can be classified as European Union Personal Data or Sensitive Personal Data (e.g., racial or ethnic origin, genetic data, biometric data, health data, sexual orientation, criminal history)?
Is client scoped data collected, transmitted, processed, disclosed, or retained that can be classified as Personal Information as defined by Canadian Personal Information Protection and Electronic Documents Act (PIPEDA) or Canadian Provincial Privacy Regulations?
Is client scoped data collected, accessed, transmitted, processed, or retained that can be classified under any other international privacy jurisdictions? If Yes, list the applicable international location in the Additional Information field.
Is documentation of data flows and/or data inventories maintained for client scoped data based on data classification?
Is there a training and awareness program that addresses data privacy and data protection obligations based on role?
Are documented policies and procedures maintained to detect and report unauthorized acquisition, use, or disclosure of client scoped data?
Does the organization have or maintain internet-facing website(s), mobile applications, or other digital services or applications that, collect, use, disclose, or retain client-scoped data that are accessed directly by individuals?
Is personal information collected directly from an individual by the organization on behalf of the client?
Is personal information provided to the organization directly by the client?
Are there documented policies and procedures regarding limiting the personal information collected and used to the minimum necessary?
Are there documented policies and procedures in place to ensure that the access, transmission, processing, disclosure, and retention of client scoped data is limited, and in compliance with applicable law?
Are policies and procedures in place to address third party privacy obligations including limitations on disclosure and use of client scoped data?
Do fourth parties, (e.g., subcontractors, sub-processors, sub-service organizations) have access to, receive, or process client scoped data?
Is there a Third Party Risk Management Program (including ongoing monitoring) in place to address data protection safeguards (administrative, technical, and physical safeguards for the security of the client scoped data?
Is there a documented policy or process to maintain accurate, complete, timely and relevant records of client scoped data?
Are there enforcement mechanisms in place to address privacy inquiries, complaints, disputes and recourse for violations of privacy compliance?
Is there a vulnerability management policy or program that has been approved by management, communicated to appropriate constituent and an owner assigned to maintain and review the policy?
Does the organization maintain policies, standards and procedures for identifying and managing cyber supply chain risks (i.e. ensuring software and hardware components used as part of delivering a service or product do not present a risk)?
Are Servers used for transmitting, processing or storing Scoped Data?
Are server security standards reviewed and/or updated at least annually to account for any changes in environment, available security features and/or leading practices?
Are all unnecessary/unused services uninstalled or disabled on all servers?
Are vendor default passwords removed, disabled or changed prior to placing any device or system into production?
Are all systems and applications patched regularly?
Are there any Operating System versions in use within the Scoped Services that no longer have patches released? If yes, please describe in the Additional Information section.
Are Windows servers used to process, store or used for scoped services?
Is there an anti-malware policy or program that has been approved by management, communicated to appropriate constituents and an owner to maintain and review the policy?
Is Unix or Linux used to process, store or used for scoped services?
Are AS/400s used to process, store or used for scoped services?
Are Mainframes used to process, store or used for scoped services?
Are Hypervisors used to manage systems used to transmit, process or store Scoped Data?
Do asset inventory and management processes include all physical objects with network connectivity (IoT Devices)?
Are Cloud Hosting services provided?
Is there a management approved process to ensure that backup image snapshots containing Scoped Data are authorized by Outsourcer prior to being snapped?
Does the Cloud Hosting Provider provide independent audit reports for their cloud hosting services (e.g., Service Operational Control - SOC)?
Now look at this and tell me we don’t have a problem... What garage-team-startup is going to be able to prioritize its time to “define and maintain policies, standards, and procedures for identifying and managing cyber supply chain risks (i.e. ensuring software and hardware components used as part of delivering a service or product do not present a risk)”, let alone even know what that strictly means? And these aren't casual questions. Behind these questions, there is a presumption of policies supported by 1000s of pages of documentation that is actively managed.
As Bill Gurley stated in summarizing regulatory capture, “Regulation is the friend of the incumbent”. Today, Salesforce has no problem answering a 200-question survey supported by 1000s of pages of documentation. They have entire teams dedicated to this function. The incumbents have only one problem with it… There simply aren’t enough questions, there should be double the number of questions, or triple...
How could you be anti-security?
I’m sure I won’t need to wait long to have people picketing my LinkedIn comments in favor of exploring such gray space as, “a wireless policy or program that has been approved by management, communicated to appropriate constituents and an owner to maintain and review the policy?” (I’m just picking these at random) I mean how does a company NOT have that in place? Especially a 4-man startup. I’m sure they genuflect before each wireless login. At the very least they should hire one more person to make sure they maintain their wireless policy. And there’s the rub. The innovators can no longer come from the grassroots to focus on solving an important enterprise problem. They have to be big players with big teams. Big money has to be on the table to even think of making anything new.
Look, nobody is suggesting that customer data should be treated without care. No business wants to be headline news about a data breach. A data breach would be devastating to a small startup, and we all know enormous data breaches happen all the time with large established incumbents. Just type data breach into Google News on any random day…
https://news.google.com/search?q=data%20breach&hl=en-US&gl=US&ceid=US%3Aen
Sure they get their fines, but who really ends up paying after standards bodies demand further bloated minutiae and organizational regulation? Is it really the incumbent or the startups that threaten market share?
The punishment for a security incident is built into the breach itself. So organizations take precautions to avoid this. But nobody, not even large corporations, is immune to a data breach, despite all these overlying precautions. Otherwise, finding such a vast daily number of top brands dealing with breaches would be more difficult.
But let’s be honest, there is no politically correct way of writing this article because it's too easy to snipe the message with the virtue signaling of "strong security." Not even your humble author can make that argument work. I’m just here to put a red flag into the ether about the death of startups in the software space.
A small light at the end of the tunnel
There is a small light at the end of this tunnel. It could be that the cloud vendors themselves could provide some relief in this situation. Snowflake is taking on this nasty juggernaut by creating a governed platform that does the shielding of data from the vendor and the shielding of IP from the client in their Native Apps Marketplace. The upshot is, that because no data is stored by the vendor, they should be able to circumvent the crazy gauntlet of cryptic policy questions. The sheer time that it has taken for Snowflake to release this marketplace is a testament to how nasty this gauntlet is to navigate. Every little feature goes through painstaking reviews, and it limits the capabilities released to app developers, but at least it gives developers a pathway to engage with customers.
The risk
Can you think of a major innovation in your lifetime that came from the bowels of a Fortune 500 company without the company founder being involved? They have to exist, but they are nowhere as prevalent as the innovative startup team. Just think of the insane GDP growth our economy has experienced just from fostering these innovations. Are we really ready to snuff out these disruptors in favor of virtue-signaled safety? The economic downside is far more dangerous. It might be time for us to unshackle the creativity that got us where we are, otherwise even the next Salesforce will have failed before it started.
Who is Intricity?
Intricity is a specialized selection of over 100 Data Management Professionals, with offices located across the USA and Headquarters in New York City. Our team of experts has implemented in a variety of Industries including, Healthcare, Insurance, Manufacturing, Financial Services, Media, Pharmaceutical, Retail, and others. Intricity is uniquely positioned as a partner to the business that deeply understands what makes the data tick. This joint knowledge and acumen has positioned Intricity to beat out its Big 4 competitors time and time again. Intricity’s area of expertise spans the entirety of the information lifecycle. This means when you’re problem involves data; Intricity will be a trusted partner. Intricity's services cover a broad range of data-to-information engineering needs:
What Makes Intricity Different?
While Intricity conducts highly intricate and complex data management projects, Intricity is first a foremost a Business User Centric consulting company. Our internal slogan is to Simplify Complexity. This means that we take complex data management challenges and not only make them understandable to the business but also make them easier to operate. Intricity does this through using tools and techniques that are familiar to business people but adapted for IT content.
Thought Leadership
Intricity authors a highly sought after Data Management Video Series targeted towards Business Stakeholders at https://www.intricity.com/videos. These videos are used in universities across the world. Here is a small set of universities leveraging Intricity’s videos as a teaching tool:

Talk With a Specialist
If you would like to talk with an Intricity Specialist about your particular scenario, don’t hesitate to reach out to us. You can write us an email: specialist@intricity.com
(C) 2023 by Intricity, LLC
This content is the sole property of Intricity LLC. No reproduction can be made without Intricity's explicit consent.
Intricity, LLC. 244 Fifth Avenue Suite 2026 New York, NY 10001
Phone: 212.461.1100 • Fax: 212.461.1110 • Website: www.intricity.com

Sample@gmail.com appears invalid. We can send you a quick validation email to confirm it's yours