The Tang Dynasty

The Tang Dynasty was a transformational moment in China. A wide variety of cultural and economic areas flourished during this time, and it launched China into a position to compete with the silk-road-enriched inner Asians.

One area that underwent such a transformation was that of banking. At the time, China issued copper coins which had holes in them. The hole wasn’t an aesthetic feature, but rather an easy way to transport large quantities of coins to use in trade. All merchants had to do was measure the string of coins to determine a fair trade had been made.
Inconvenience Breeds Innovation

There were some very inconvenient realities about carrying strands of copper coins around, they’re heavy, difficult to discreetly transport, and hard to store.
During the Tang Dynasty merchants would leave their coins with trustworthy individuals. To track this money these trustworthy “bankers” would issue a paper certificate validating how much money was being stored. Over time, people began to trade the certificates rather than trading the coins themselves. Not only was the certificate more convenient, but it also kept the coins safely stored. This practice gained so much popularity that by the year 812 the Chinese government took over the issuing of paper bank drafts. I’m sure back then that there were people saying. “I don’t like the bank because I don’t want my money in someone else’s hands.”
But this fundamental change greased the skids for trading to scale, and I would argue that it was at the foundation of economic success in the Tang dynasty, and the others to follow.
Corporations find themselves in a similar scenario as the merchants of old. But today the burden they carry is that of the corporate data center. The cost of ordering enterprise class servers and dealing with the physical security burden of the data center is like carrying the copper coins around. Like the bankers of old, cloud vendors are offering an alternative way to store data. Their physical facilities are far more secure than the ones corporations can muster, and provisioning additional hardware capacity is exponentially faster.
Cloud vendors have an even greater proposition to offer beyond just providing rented server capacity. If organizations are willing to refactor their storage and compute, the cloud can transform the way companies do business. See the cloud offers the ability to flexibly allocate computing resources on an as-needed basis. This flexibility lowers the risk to business initiatives by allowing organizations to experiment with little to no financial commitment. If the initiative is successful, than the company can naturally scale, if the effort is not successful than little was spent. This provides far more agility compared to the typical effort which requires some arbitrary forecast for how much computing horsepower a given initiative will need.
Examples
Sometimes it's hard to really envision what this means for an organization, let me try and use a few concrete examples:
A few months ago I was interviewing a Chief Financial Officer (CFO), and He shared with me a project the Chief Marketing Officer (CMO) took on. The request for multiple high performance custom servers came across his desk, which came to the tune of nearly 2 million dollars. The CFO granted 400,000 dollars to the project because the potential usage was still up for debate. The CMO insisted that this limitation would put her entire project at risk, and after a lot of executive posturing, the CFO signed off on 1.5 million dollars of hardware. As the launch of the campaign progressed, it started to become clear that the organization had funded a boondoggle. The servers went almost completely unused and the CFO had 1.5 million dollars of servers on his hands.

While that story is sinking in, let me share an alternative story.
Intricity recently lead the development of an IoT solution for a fortune 1000 manufacturing organization. After Intricity assisted the organization in identifying a chosen cloud vendor, the joint development began. From the architecture all the way down to the development of the entire application stack, the total spend for hardware and software was almost non-existent. In fact, the footprint of the effort was so small that the cloud vendor reps had a hard time locating the project itself. However, when it came time to go live, the IoT deployment was ready for scalability which had no ceiling. As users came onto the system the cloud deployment would dynamically allocate additional Hardware as needed. Then shut down that hardware when it was not. Additionally, Intricity designed their cloud deployment to leverage as many native cloud services as possible which had no server allocation. Thus the organization was paying for the lightest possible hardware footprint to service the IoT solution.
“Your” data
 I often hear business leaders saying, “I don’t like the cloud because I don’t want my data in someone else’s hands.” However, when you weigh the operational and financial benefits of moving to the cloud, the fear needs to be closely analyzed and justified. For example, one of my first responses to such an objection is, “What makes the data “yours”? Is it the fact that you own the lease on the data center? Or is it because you originated the data?” Of course neither of these things really have anything to do with you retaining your data. A hacker doesn’t share those sympathies. Additionally, data has properties which make it unlike any other asset within a corporation. For example, I can make a perfect copy of data with no effort, and I can transport it at speeds which have no parallel in the physical world. With such properties, the physical location of data is a meaningless token of ownership. Thus, the only thing that makes data yours is security.
I often hear business leaders saying, “I don’t like the cloud because I don’t want my data in someone else’s hands.” However, when you weigh the operational and financial benefits of moving to the cloud, the fear needs to be closely analyzed and justified. For example, one of my first responses to such an objection is, “What makes the data “yours”? Is it the fact that you own the lease on the data center? Or is it because you originated the data?” Of course neither of these things really have anything to do with you retaining your data. A hacker doesn’t share those sympathies. Additionally, data has properties which make it unlike any other asset within a corporation. For example, I can make a perfect copy of data with no effort, and I can transport it at speeds which have no parallel in the physical world. With such properties, the physical location of data is a meaningless token of ownership. Thus, the only thing that makes data yours is security.
 Firewall
Firewall
If you own your datacenter then you’re counting on your firewall to protect your data. The internet is a hostile medieval mess, so having a strong firewall makes all the sense in the world. Hackers are constantly on the lookout for soft targets and big payoffs.

I often like to think of a firewall like the walls of a castle. Each company has their walled in city of employees which are protected from the medieval mess outside. However, each one of these kingdoms (corporations) needs to be able to interact with each other. To do this, they need gates in the wall to ensure they can get vital assets in and out.
If an imposter can get within those walls, they can access data, users, applications, and stay parked until the opportune moment to plan their attack. The same is true for the firewall, once a hacker has gotten past the firewall, they can access the persistent application servers which have sensitive data and work towards the opportune hack which will compromise your organization.
 Encryption
Encryption
Encryption is the primary way which cloud vendors secure data. This is done by creating a mathematical algorithm which unscrambles the data. This approach has been used for centuries. Julius Caesar used ciphertext in his private correspondence. The technique would shift the alphabet so that messages would appear as a mess of random letters. On the receiving end you had to know that the last three letters of the alphabet had been shifted to the first positions. This rendered messages unreadable during transport. Here’s an example:
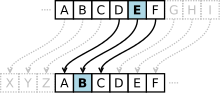
Plaintext: THE QUICK BROWN FOX JUMPS OVER THE LAZY DOG
Ciphertext: QEB NRFZH YOLTK CLU GRJMP LSBO QEB IXWV ALD
However, the encryption leveraged today uses a far more complicated cypher which can only be determined by using a two key system. One key being a public key which is publicly visible and the other being a private key which only the receiver should have. The public key can only be opened with a private key and the private key can only be opened with a public key. By combining the receiver's public key with the sender's private key you can send messages to a recipient and the recipient can know for sure that the sender was who they think it is. Here’s a good video explanation of the process: https://www.youtube.com/watch?v=r4HQ8Bp-pfw

Cloud vendors use encryption to secure the data in their data centers, and ensure that only the organization which owns the data is accessing the data. However, it’s important to point out that the definition of “what data is encrypted”, and “what level of encryption”, is a decision that is left in the hands of each customer. For example, you can encrypt data at rest (not being used and just sitting in storage) or in flight (being used in a compute process). The cloud vendor leaves this up to each customer.  Because the management of the data’s virtual security is left up to each customer, the cloud vendor has no master key. Thus even though the cloud vendor is physically housing all the data on their servers, they can’t access it. THIS is why you don’t see hacks to cloud datacenters where ALL the customers are impacted, there just is no “master key” to all the data.
Because the management of the data’s virtual security is left up to each customer, the cloud vendor has no master key. Thus even though the cloud vendor is physically housing all the data on their servers, they can’t access it. THIS is why you don’t see hacks to cloud datacenters where ALL the customers are impacted, there just is no “master key” to all the data.
Small is Beautiful
 As interesting as these different security options are, there’s a more practical reason why a refactoring for cloud services is more secure… its small. See if I’m using ad-hoc services which are designed to not have a distinct home which they run on, my footprint is very small.
As interesting as these different security options are, there’s a more practical reason why a refactoring for cloud services is more secure… its small. See if I’m using ad-hoc services which are designed to not have a distinct home which they run on, my footprint is very small.

Take for example a data transformation routine. If you have a dedicated server with a specific IP address which handles the movement and transformation of your data, than you have an easy target. On the other hand, if you have a data transformation service, which pops into existence when its called then disappears when it's done, you have a very small vector to attack.
Now compare that to the WHALE your firewall is… This giant wall, holding a treasure trove of information, waving its flag for every hacker to see. This is what your data center is sitting behind! THIS is the primary security justification for refactoring your footprint to work in the cloud. If you put yourself in the shoes of a hacker what target would you go after? A service with intermittent points of existence, or a slowly moving behemoth which has servers that stay put?
Baby Steps
Getting to the cloud is a multi stage event, but this is where Intricity can help produce the wins that will get the support from your organization, to accelerate that process. The key is a clear demonstration of value. An ideal first project is a cloud data lake and data warehouse. Intricity can deliver a fully cloud enabled and refactored environment even if the source data sits in a hybrid of on-premise and cloud applications.
I recommend you reach out to Intricity to Talk with a Specialist about your specific scenario, our experts can guide you step by step through the value curve.
Who is Intricity?
Intricity is a specialized selection of over 100 Data Management Professionals, with offices located across the USA and Headquarters in New York City. Our team of experts has implemented in a variety of Industries including, Healthcare, Insurance, Manufacturing, Financial Services, Media, Pharmaceutical, Retail, and others. Intricity is uniquely positioned as a partner to the business that deeply understands what makes the data tick. This joint knowledge and acumen has positioned Intricity to beat out its Big 4 competitors time and time again. Intricity’s area of expertise spans the entirety of the information lifecycle. This means when you’re problem involves data; Intricity will be a trusted partner. Intricity's services cover a broad range of data-to-information engineering needs:
What Makes Intricity Different?
While Intricity conducts highly intricate and complex data management projects, Intricity is first a foremost a Business User Centric consulting company. Our internal slogan is to Simplify Complexity. This means that we take complex data management challenges and not only make them understandable to the business but also make them easier to operate. Intricity does this through using tools and techniques that are familiar to business people but adapted for IT content.
Thought Leadership
Intricity authors a highly sought after Data Management Video Series targeted towards Business Stakeholders at https://www.intricity.com/videos. These videos are used in universities across the world. Here is a small set of universities leveraging Intricity’s videos as a teaching tool:

Talk With a Specialist
If you would like to talk with an Intricity Specialist about your particular scenario, don’t hesitate to reach out to us. You can write us an email: specialist@intricity.com
(C) 2023 by Intricity, LLC
This content is the sole property of Intricity LLC. No reproduction can be made without Intricity's explicit consent.
Intricity, LLC. 244 Fifth Avenue Suite 2026 New York, NY 10001
Phone: 212.461.1100 • Fax: 212.461.1110 • Website: www.intricity.com